Product personnel should find a balance between protection and user experience, and choose according to their own product characteristics.
As an important identity verification tool, SMS verification code has been widely used by developers due to its easy operation, high security, and strong timeliness. However, due to its convenient access and fewer restrictions, it is easy to be used by criminals to bombard text messages, maliciously brushing off a large amount of text messages, causing a large amount of money loss to the company or individual. The main reason for this situation is that in the actual product design process, some The product personnel did not know much about the technical implementation and had a weak awareness of prevention. They simply or simply ignored the restrictions on the SMS verification code, which caused the SMS interface to be maliciously used by criminals.
Before introducing the anti-swipe strategy, we need to understand the common behaviors of swiping SMS verification.
1. Swipe the SMS verification code for the purpose of attacking the mobile phone number
The main target of this type of attack is that the attacker uses the SMS interface of the web site to bomb the target mobile phone number by SMS. The attacker will first collect the SMS interface of multiple unprotected websites on the Internet, set the mobile phone number to be attacked by simulating the user, and cyclically send SMS verification code requests to the background to achieve the purpose of attacking the mobile phone number. For this type of attack, the purpose of protection can be achieved by setting the general verification code.
2. Attacks for the purpose of maliciously scraping the SMS fee of the target website
The main purpose of this type of attack is to wipe off the SMS fee of the target website. On the basis of the first type, the attacker will constantly change various interface parameters such as mobile phone number, IP (using a high hidden proxy), etc. to request the background to send SMS verification codes. To scan text messages maliciously, the background is unable to distinguish the authenticity of the user. The target of the attack is clear and it is difficult to defend. Because it changes different IPs and mobile phone numbers, some simple measures are basically ineffective. Product designers need to pay special attention to this type of attack during the early product design.
The following are some countermeasures against attackers.
1. Add graphic verification code on the front end
It is a common method to add a graphic verification code before obtaining the SMS verification code. Attackers generally use automated attacks. After the graphic verification code is added, the attacker must identify and verify the verification before it can simulate the user’s sending request. This step needs to be performed on the page, and automated attacks cannot be used. The first type of attack basically fails, and at the same time it will increase the cost of the second type of attack (it may be verified by manual coding). When choosing a verification code, you should consider both the smoothness of the user’s operation process and the security.
The following picture shows several common graphic verification codes, which can be selected according to the characteristics of their own platforms.
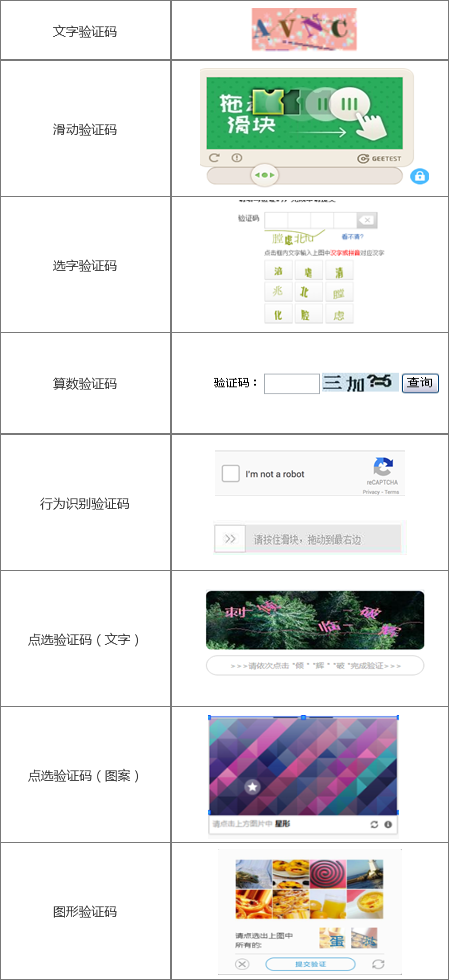
2. Limit the number and time interval of receiving SMS per day for a single mobile phone number
Limiting the number of times a single mobile phone number can receive per day can prevent a single mobile phone number from swiping text messages without limitation. At the same time, setting a time interval can be effective to prevent manual ticket swiping. The number of SMS receipts can be limited according to the characteristics of the platform. Generally, the number of verification codes accepted per day is about 10; the interval for sending the same number is usually 60 seconds. Kind of low-level error.

3. Restrict IP
Limiting the maximum sending volume of a single IP can effectively prevent the issue of multiple phone numbers being swiped under a single IP. The maximum sending volume limit is to prevent malicious attackers from swiping SMS verification codes with different mobile phone numbers under the same IP. According to the actual situation of the platform, a threshold for the maximum sending volume of short messages is designed. If the threshold is exceeded, no short messages will be returned.
4. Limit the registration process
Generally speaking, the most frequently attacked place is the registration page, and the triggering process is generally limited from two aspects.
- The first is that you can write instructions from the front end and only allow you to jump to the registration page on the official website homepage;
- The second method is to carry out the registration process step by step, first set the account password, and then the next step of SMS verification can be carried out after the setting is successful.
The two methods of increasing the preconditions and increasing the difficulty of the attack can effectively prevent automated attacks. It should be noted that the two methods have more or less impact on the user experience, and the product manager needs to choose according to the characteristics of his own platform.
5. Uniquely identify the sender
In order to prevent the second type of malicious attackers from modifying the parameters transmitted to the server, causing multiple IP and multiple mobile phone numbers to swipe the SMS verification code, the background should verify the parameters passed from the front desk. The method is generally to use the token as unique identification verification. The backend writes an algorithm to inject the token into the front end, and then the front end can obtain the token through corresponding rules. When sending the SMS verification request interface data, bring the token, and perform the token on the back end. Verification, the SMS can be sent normally only after the verification is passed.
In the product design process, the first three methods are generally used in combination, which can basically prevent most malicious SMS verification codes. Product personnel should find a balance between protection and user experience, and choose according to their own product characteristics.

